When you deploy an AWS Organization using Control Tower, an AWSSSO IdP is created in every account. It’s name ends with DO_NOT_DELETE. What happens if you delete it?
Background
I recently had someone reach out to me asking what happens if the auto-created AWS SSO IdP Provider that integrates with IAM Identity Center in Control Tower environments is deleted. There was a belief that an AWS account could only connect to a single Identity Provider and in order to perform test Okta capabilities, the IAM Identity Center Provider was deleted.
The Error
If the AWS SSO Identity Provider is deleted, you’ll see an error message like the one below if you attempt to login to the account via the AWS Identity Center access portal:
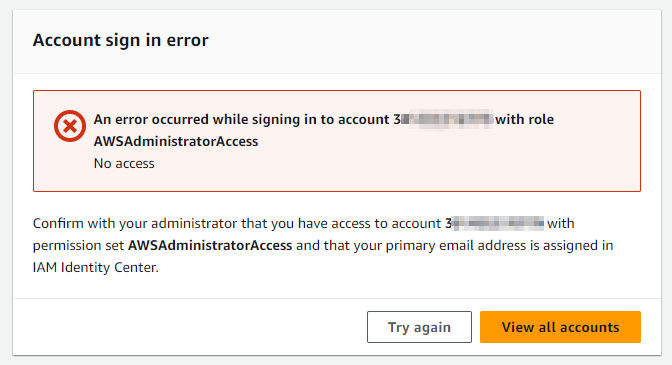
The Fix
Fortunately, at least in this case, the recovery steps were simple:
- Login to the AWS Management Account (from which Control Tower was deployed)
- Open the Control Tower service dashboard and click Organization in the left-hand navigation pane
- On the Organization pane, select the account with the deleted AWSSSO IdP, and then click Actions | Update
- Scroll to the bottom of the Update account page and click Update account
- You should see a message that states it is possible to update 5 accounts at the same time. Review the text and then click Update account. In my case, the Service Catalog update task lasted about 7-10 minutes.
- When the account update completes, you should see a Success notification within a green bar
- Attempt to login to the updated AWS account
After performing the steps above, the AWSSSO…..DO_NOT_DELETE Identity provider was restored and I could successfully login to the formerly unreachable AWS account through the access portal.

